Tips: Secure Your Wireless Connection with WPA/WPA2 Encryption
Leaving your wireless internet unsecured lets anybody access your network which can cause slow connection speeds.
If an intruder illegally downloads something using your wireless internet, you could be legally liable for their actions.
An intruder could potentially monitor your network traffic and obtain passwords or other confidential information.
WEP encryption can be easily cracked in a matter of minutes, which makes it only slightly better than an unsecured connection.
This guide will show you how to identify the current security used on your wireless network, and how to better secure it with WPA / WPA2 encryption.
Identifying Your Current Security Mode
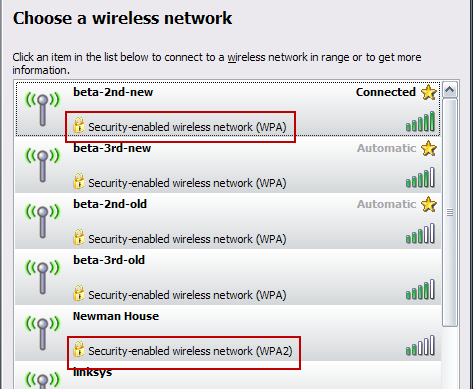
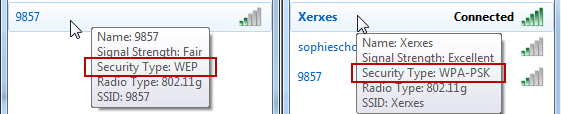
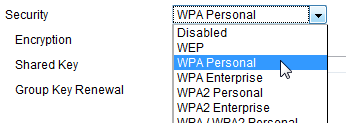
Most of the time, you can see what type of security an access point uses before connecting to it. View your available wireless networks and check out your own network to see what your current security settings are.
If you see WPA or WPA2 next to your connection – that’s great, you’re done. WPA and WPA2 provide strong protection as long as you use a good password. When creating a password, avoid using dictionary words and try to include complex characters like !@#$%^&*.
If you see WEP or no security, it’s time to add WPA or WPA2 to your access point.
Enabling WPA/WPA2
Wireless security options are different for every access point and router, so refer to your user’s manual or check out the device manufacturer’s support information online. Your device may even come with an installation disc that can walk you through security setup.
In general, you need to locate a Wireless/Wireless Security section in your access point’s configuration and enable WPA or WPA2 security. With many access points and routers, you can type in the Gateway address of your internet connection in a web browser to access the device’s configuration page.
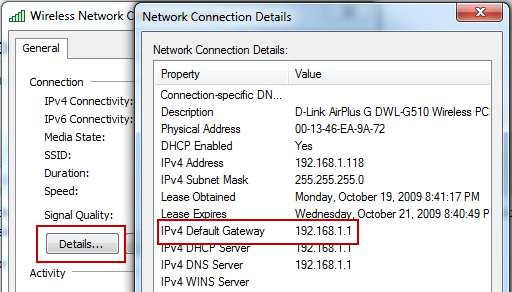
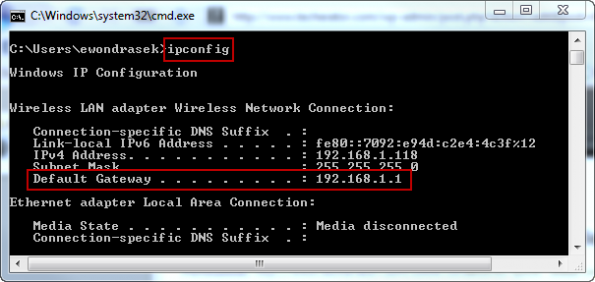
Note: The Gateway address can be found by viewing your current connection’s details (varies by your operating system) or by pressing Windows Key + R, type cmd and press enter, then type ipconfig and press enter.
In my case, my router’s address is 192.168.1.1, so I typed that address in my browser and pressed enter. This will open the device’s configuration page (you may need to enter login credentials to access this page). Locate a Wireless Security section (this may be under Wireless, look around until you find it) and enable WPA or WPA2 security, selecting ‘Personal’ if it gives you the option. Create a strong password and click save. You will have to re-join your network once this has been done.
Have any tips for better securing your internet connection? Share them with us in the comments.
From: Techerator!
Implement switch security on your network
When it comes to securing internal networks, one area that organizations often overlook is switch security. Most companies tend to focus on their borders and end users, forgetting the devices that connect the two.
Ensuring switch security in your organization basically comes down to two steps: Defining what users can see, and defining what they can connect.
What you see
Every business-grade switch allows you to define virtual local area networks (VLANs). Organizations typically implement VLANs for the following reasons:
Broadcasts: A VLAN doesn't pass broadcast traffic to nodes that aren't part of the VLAN.
Performance: A VLAN can reduce the number of router hops and extend your local topology between user workstations and resource servers, increasing the apparent bandwidth for network users.
Departments: A VLAN can segment departments that use bandwidth-intense applications. You can also dedicate a VLAN to specific types of job roles (e.g., executives, kiosk workstations, etc.).
Security: A VLAN allows organizations to separate sensitive clusters of systems from the rest of the network, decreasing the likelihood that users will gain access to information on these clients and servers.
What you connect
Port security is also available on every business-class switch. Some switches allow very in-depth settings; others just provide some of the basics. Here's a look at some of your options:
MAC Locking: This involves tying a Media Access Control (MAC) address of one or more connected devices to a physical port on a switch. If you lock a switch port to a particular MAC address, you don't have to worry about superusers or internal black hats creating backdoors into your network with rogue access points.
MAC Lockout: This disables a specified MAC address from ever connecting to a switch.
MAC Learning: Using knowledge about each switch port's direct connections, the switch can set security based on current connections.
Remote Configuration: Limit remote configuration to specific IP addresses, using SSH instead of Telnet. Telnet passes usernames and passwords in clear text, potentially allowing everyone on the LAN segment to see login credentials.
Final thoughts
Switch security does involve challenges, particularly when it comes to setting up and deploying new workstations in your help desk area. This is definitely an issue you should consider when implementing a switch security policy.
Network administrators who balk at port security because it's labor-intensive and requires constant management should consider this: Port security stops people from attaching wireless access points and bypassing your site security. That alone should be a good enough reason to implement switch security on your network today.
By Michael
Security Of Instant Messaging Cannot Be Ignored
Labels: Instance Message Security
Instant messaging policies
The first step is to clearly state your organisation's policy on instant messaging. Can users install and use IM software on systems owned by the organisation? If you have a strict "no outside software" policy, you may think you're covered, but keep in mind that Windows XP SP2 ships with Windows Messenger installed, creating a policy loophole.
Here's a set of questions you should consider when defining your organisation's IM policy:
Is IM use permissible on your network?
May users run IM software on systems owned by your organisation?
Does the organisation endorse/require a specific IM platform?
Is encryption mandatory?
Is IM acceptable for corporate use or for personal communications only?
Are there restrictions on the sensitivity of data that may be communicated via IM?
Is there a requirement to retain records of IM communication for any period of time?
Once you have a clear policy on IM use, educate your users on policy requirements and their responsibilities.
Instant messaging security measures
If you decide to allow instant messaging, blanket it with layers of protection to ensure you're organisation is protected against the viruses, worms and other malicious code that's become prevalent on IM networks. Run a modern antivirus program that includes IM scanning on all workstations, and consider a using network-based content filter that scans IM traffic for malware.
You also want to prevent the threat of eavesdropping on your traffic as it traverses public networks. Out of the box, IM software uses public servers hosted by the IM provider, which means all messaging must traverse the public Internet on its way to and from the server. If you think your users might send sensitive messages through IM (accidentally or intentionally), you should strongly consider encrypting that traffic. Unfortunately, encrypted IM is a relatively immature technology that typically requires a specialized client. One standout in this field is the free Trillian client by Cerulean Studios, which supports multiple IM networks and allows encrypted communications with other Trillian users.
The ultimate option in secure instant messaging is to run your own managed IM server or gateway. This eliminates the threat of outsiders intercepting internal messages as they cross the Internet by keeping the traffic on the local network, and it's actually easier than you might think. Many of these products allow you fine-grained control over the types and destinations of IM traffic on your network. In addition to the commercial products available, you may wish to consider the open-source Jabber IM server project.
Instant messaging is here for the foreseeable future and poses a significant challenge to information security professionals. If you're not able to block IM completely due to business requirements, you should certainly consider implementing strong controls to limit the risk this technology poses to your organisation.
Recommanding a program, Colasoft Capsa, to check if your IM is communicating safely.
By Mike Chapple From SearchSecurity
How to Monitor Internet Traffic with Network Analyzer
In case we want to monitor internet traffic generated or is generating in LAN, here is a detailed process how we can do it with Colasoft Network Analyzer – Capsa.
Again we must make sure the network analyzer software is correctly implemented so we can capture all the traffic in LAN, if you don’t know how to do it, please make sure you read how to implement a network analyzer.
First let’s launch a new project with Colasoft Network Analyzer, then do some online activities, such as chatting, browsing a website, sending and receiving emails, downloading some files. All these activities will generate different kinds of internet traffic. We may keep the project running to continuously monitor internet traffic or stop the project to do some analysis.
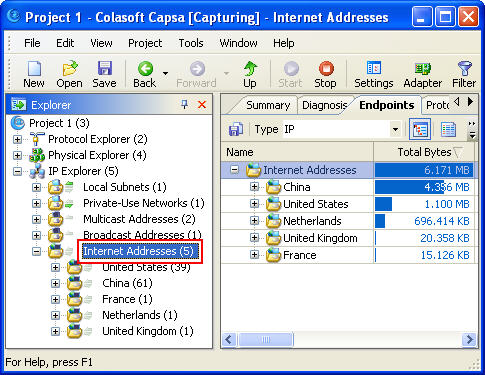
To monitor internet traffic, we’d better first select the “Internet Addresses” in the “Explorer” on the left window:
We can see that all the internet addresses are listed by countries, to monitor internet traffic of a specific country, we just need click on it; If we want to monitor internet traffic of a specific IP address within one country, we need to expand the country node and select the IP address in it.
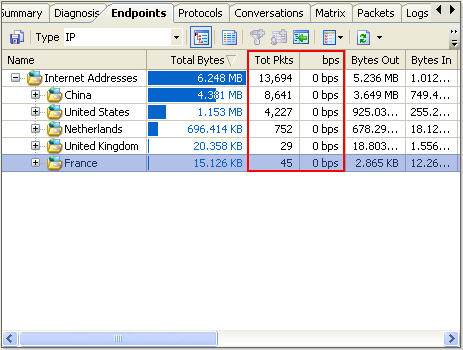
Also we can monitor internet traffic aggregated or internet traffic in real-time
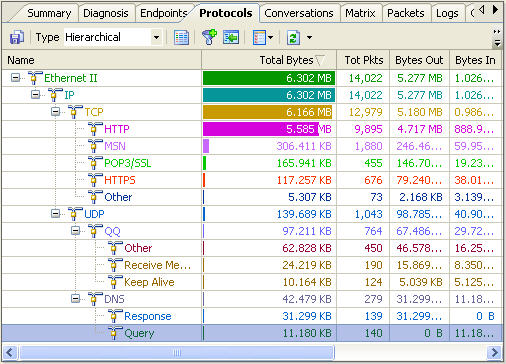
To view what online activities have generated or are generating internet traffic, we need to use the “Protocols” Tab.
We can see there are protocols which separately stand for different internet activities:
HTTP – Website browsing
MSN – online chatting with Live Messenger
POP3 – Email
HTTPS - Website browsing via a secure link
QQ- online chatting with QQ
DNS – Domain Name System
About Capsa
Colasoft Capsa is a network analyzer (packet sniffer or protocol analyzer) designed for network monitoring and troubleshooting. It performs packet capturing, network monitoring, protocol analyzing, packet decoding, and automatic diagnosing. By giving users insights into all of network's operations, Capsa makes it easy to isolate and solve network problems, identify network bottleneck and bandwidth use, and detect network vulnerabilities. Learn more about Capsa, please visit Colasoft.com
How to Monitor HTTP Traffic with Network Analyzer
In order to monitor http traffic, we will need a network analyzer (or a protocol analyzer) software. Here is a detail process how we can monitor http traffic in LAN with Colasoft Network Analyzer – Capsa.
Again let’s launch Colasoft Network Analyzer and start a new project. Don’t forget one thing, we have to deploy the network analyzer to the mirror port of the core switch in order to monitor all http traffic in LAN, if not, we can only monitor http traffic of our own computer.
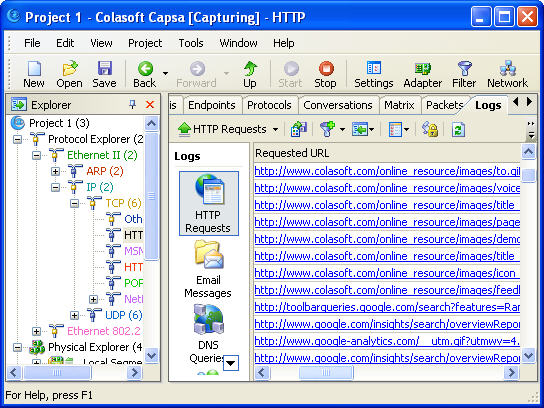
Then let’s start browsing a website, for example, www.colasoft.com, to generate some http traffic. Now let’s get back to the network analyzer and see if there is http traffic. OK, we can see the network analyzer has already captured some http traffic in the “Protocols” Tab
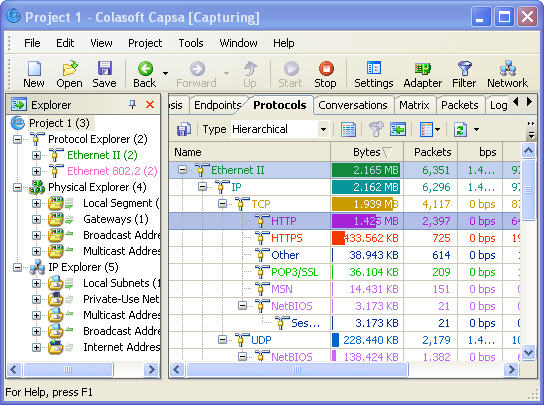
We can see both the aggregated http traffic since start capturing and the real-time http traffic in this tab.
If we want to do a deeper analysis on http traffic, we will need to use the “Locate” function to locate http protocol in the Explorer to let the network analyzer display only the data that is http protocol. Right click on the protocol and select “Locate Explorer Node” in the pop-up menu.
If we want to know who are using http protocol and what they are actually browsing, we are going to use two tabs, the “Endpoints” Tab and “Logs” Tab.
Let’s see who are using http protocol:
And what they are actually browsing:
What Can Hackers Do With a Network Analyzer
Labels: credit card, hacker, network admins, network analyzer, password
Security breaches of all kinds are reported all the time. Everyday we hear of hackers who managed to steal sensitive data, of people who become victims of identity theft, etc. Very often the breaches are so incredible that you wonder if hackers have supernatural powers. Well, hackers hardly have supernatural powers but they don't need them –supernatural powers are not necessary when a networklacks security and one has the right tools to break in.
Hackers Monitor Networks With a Network Analyzer
The tools hackers use to break into networks are more or less the same tools network admins use to monitor and maintain their network with. For example, network analyzers are among the tools hackers love most. A network analyzer captures packets and shows you their contents.This means that with the help of a network analyzer running somewhere into the network, hackers can monitor all the unencrypted traffic to and from this network.
This is really scary – just imagine a malicious hacker who knows all the secrets of your company. It gets even more dangerous for networks, where hubs (and not switches) are used because in this case a network analyzer can be installed on any computer and the hacker will monitor all the traffic in that segment, not only the traffic to and from the host. The good news is that hubs are almost out of use today and because of that hackers can do less damage with a network analyzer.
Hackers Obtain Passwords and Credit Card Numbers With a Network Analyzer
When a hacker uses a network analyzer to monitor your network, this is not nice but when he or she steals passwords, credit card numbers and other types of sensitive data, this is a real danger. Unencrypted passwords, credit card numbers and other sensitive data are an easy target for a hacker with a network analyzer.
In many of the cases of mass theft of credit card numbers and passwords happen because hackers use a network analyzer on an unencrypted network. For truth's sake, it is important to mention that even if all the traffic is encrypted, there are still many other ways to obtain sensitive data. But when the traffic over a network is not encrypted and nobody monitors the network for unauthorized network analyzers, sooner or later data will be stolen.
One of the greatest achievements for hackers with a network analyzer is to capture the administrator's password. When the administrator's password is transmitted over the network in an unencrypted form, this is an easy target for hackers. If hackers manage to intercept the admin password, they have the power to do everything they want to on your network – delete data, modify data, etc. So, do you see why hackers don't need supernatural powers but only the admin password?
5 Things Our IT Department Have to Skip
 In last blog, we have talked about the 5 items our IT department must do even in the big recession, in addition to the things we can't do without, there are many more things we had to skip. We are not exactly happy to stop doing these things but desperate times cry for desperate measures and since these activities are something we can do without we had to either quit them, or drastically reduce them:
In last blog, we have talked about the 5 items our IT department must do even in the big recession, in addition to the things we can't do without, there are many more things we had to skip. We are not exactly happy to stop doing these things but desperate times cry for desperate measures and since these activities are something we can do without we had to either quit them, or drastically reduce them:
No purchases of new hardware. Though it is not precise to say that we haven't bought a single piece of hardware in the last year, we have definitely cut hardware spendings. For the time being we do not plan to make major hardware purchases.
Capital expenditures. Capital expenditures are another budget item we had to drastically shrink. We had schedules projects but the current economic situation made us have second thoughts and now capital expenditures are on hold.
Software that is nice to have but we can do without it. Similarly to hardware and capital expenditures, some major software expenses had to be cut. Yes, there are many products, for instance accounting, HR, or ERP modules, which are great to have but we'll go for them when the economic outlook is less gloomy.
Standardization. You know that IT people generally hate when they have to deal with bureaucracy and standardization, so if there is an item, we are happy to skip, this is standardization. More or less we skipped all standardization-related activities except those, that are related to regulations compliance. Standardization is put on hold, especially if it requires investment or other resources.
No infrastructure upgrades. We are not exactly happy about this one but since there are more important items we can't skip, we had to significantly reduce the planned network upgrades. Some of the projects in this area are put on hold, while others are canceled.
James Ackland is Author of this article from http://www.colasoft.com/?prid=02060001.
About Colasoft Co., Ltd.
Ever since 2001, Colasoft has been dedicated in providing all-in-one and easy-to-use network analyzer software for network administrators and IT managers to monitor network activities, analyze network performance, enhance network security, and troubleshoot network problems. Up to now, more than 5000 customers in over 70 countries trust the flagship product – Colasoft Network Analyzer as their network monitoring and troubleshooting solution. Colasoft also offers four free network utilities: Colasoft Packet Builder, Colasoft Packet Player, Colasoft MAC Scanner, and Colasoft Ping Tool. Learn more about Colasoft and its solutions, please visit http://www.colasoft.com/?prid=02060001.
Best 101 Free Computer Software For Your Daily Use
Good things in life do not necessarily cost you a bomb. Below I have compiled a list of the top 101 free computer software you can make use of.
Enjoy!
Office Suite
Security
Desktop management
Browser
Fun and Games
Graphics Editing
Video and Audio
PDF creator
Virtual Server
Instant Messaging
Download manager
File Management
Torrent Manager
Backup Program
File Compression
System Optimization and Diagnostic Tool
Email Client
Photo Organizer
Video Converter
FTP client
EyeCandy
Thanks to Frank for recommending another free software. Here is it:
How To View MSN Chat Logs Through Network Analyzer
Three most popular Network Analyzer, Sniffer Pro, Omnipeek and Colasoft Network Analyzer, are adopted with customizing a filter as the first step only to capture the data communication of MSN Protocol. In Omnipeek and Colasoft, we can directly select MSN in protocol filter, while in Sniffer Pro, no MSN Protocol can be found, but we can customize a Port filter of 1863port since TCP 1863 Port is the default operation route for MSN. Then, synchronously run three software sniffing and test MSN in local computer. Later, some data packets of MSN will be captured and then stop capturing to analyzing packets captured. According to some material, we found that MSN is encoded during Password Authentication phase, while all other information are not, and messages will begin with “X-MMS-IM-Format”. Search “X-MMS-IM-Format” in these analyzers adopted, results are listed below.



Messages captured by all three analyzers are shown to be unanimous. The highlighting part in the picture is the chat logs of MSN. And you can see corresponding ASCI data.
Chatting Specifics are still unavailable from the above shown data (For English and Numbers, chat logs can be found directly through ASCI decoding.), they need format converting with a tool named SmartConvert is add to the operation and the contents after converting are as follows through which a clear chat log of MSN is visible.
Meanwhile, there is still another way of viewing original messages, from MIME-Version: 1.0 we can see the data using the MIME format, that is, Mail Format, thus, exporting this data packet (any format), then converting it to eml and finally running it with Outlook or Foxmail.
All steps introduced above are the whole course for the test of capturing and analyzing of MSN, through these easy steps, one can have a thorough perspective of MSN communication in internet.
Colasoft Network Analyzer - Capsa
Capsa is an easy-to-use Ethernet Network Analyzer (packet sniffer or network sniffer) for network monitoring and troubleshooting purposes.
It allows you to monitor network operations, isolate & solve network problems, identify network bottleneck & bandwidth use, and detect vulnerabilities.
It performs real-time packet capturing, 24/7 network monitoring, advanced protocol analyzing, in-depth packet decoding, and automatic expert diagnosing.
KeyFeatures
Traffic Statistics & Bandwidth Use
With Capsa's network traffic monitor feature, we can quickly identify network bottleneck and detect network abnormities.
Advanced Network Analyzer
Being able to support more than 300 protocols in the latest version, Capsa make it easy to analyze protocols in network and understand what is happening.
In-depth Packet Decoding
As a Network Analyzer, Capsa is able to capture all network packets transmitted on network and displays detailed packet decoding information in Hex, ASCII and EBCDIC.
By giving you insights into all of your network's operations, Capsa makes it easy to isolate and solve network problems, identify network bottleneck and bandwidth use, and detect network vulnerabilities
Monitor Multiple Network Behaviors
Colasoft Capsa can record global or scope-specific network events, containing many types of log primarily generated by the advanced analyzers: HTTP requests, email messages.
Automatic Expert Network Diagnosis
Capsa is able not only to automatically detect and clearly identify network events but also suggest corresponding solutions. You may also set your own thresholds according to your network's characteristic.
Visualize all Connections in Matrix
"Matrix" is a view that visualizes all network connections and traffic details in one single graph. The nodes around an elongated ellipse display the hosts in your network....
Who use Capsa?
Network administrators can directly monitor http requests, email messages, DNS queries, as well as real-time activities and message details for the four most popular instant messengers: MSN, AIM, ICQ, and Yahoo Messenger.
Capsa is designed to be used by both IT professionals and novice users.
Whether you're a network administrator who needs to identify, diagnose, and solve network problems quickly, an IT professional who wants to monitor user activities on the network, a security manager who needs to ensure that the corporation's communications assets are safe, or a consultant who has to quickly solve network problems for clients, Capsa has the tools that you need.
Capsa has the tools that you would not find in other network analyzers, including tools to create and replay packets, and ping and scan IPs and MACs across the LAN.
What separates Capsa from other network analyzers is its unique ability to conduct quick drilldown analysis on a single workstation, protocol or packet.
Why Choose this Network Analyzer?
Quick Drilldown Analysis
Unique ability to conduct quick drilldown analysis on a single workstation, protocol or packet, allowing you quickly isolate network problems.
Pure Software Solution
Easy to install and deploy, regular and beneficial updates, no need to purchase expensive hardware devices.
Easy to Use
No training needed, no profound background required, data are displayed in intuitive tables and graphs; almost all customers comment Capsa as "easy to use".
Timely Support
Colasoft technical support team and customer service team are constantly dedicated to answering your questions regarding network troubleshooting and network analysis, for free.
Latest User Opinions
• Recommended Software by User yayaya
The price is reasonable for this product has the perfect functions, such as real-time capturing and expertise diagnosis for our network which really meet our requirements!
• Good performance and capability of diagnosing and troubleshooting by User Guferer
After using Colasoft Capsa, we found that this product can not only support the real-time capturing and continual monitoring for our network, furthermore, it has the excellent capability of protocol analyzing (approximately 300 types) and packet decoding! So incredible performance it is! Well, the most exciting part is the automatic expert diagnosing! That really saves so much money and time for me, and I do not worry about the solution of failure again!
• Download Colasoft Trial and Try by tgh12
The software is good
Top 5 Items Our IT Department Must Do
We can't say that the recession took us by surprise but certainly we didn't expect it to be that fierce. However, recession or no recession, life must go on and if a company wants to make it, there are many things which can't be skipped. So, no matter that IT budgets are tight, there are items a company can't save on. Here are the top 5 items our IT department will not sacrifice:
1, Network security and security in general. Being in the network security business themselves, we know that network security and security in general is paramount and no matter how hard the economic situation might be, this is not an item to save on because the price is too high. Certainly, we are not buying the most expensive solutions, even though they are incredibly great but we also do not make compromises with the quality either.
2, Going green. Going green is also an item we can't skip. Green technology saves money and now this benefit is more important than ever. So, if we buy new IT stuff, we definitely go for the green items.
3, Compliance. Regulations compliance is another item we can't afford to skip, unless we really want to go out of business (and we don't). So, when there are steps in this direction to be taken, we do them – no way!
4, Training. Training is also important and even though our training budget has shrunk, we still try to keep our staff qualified.
5, Outsourcing. Outsourcing has been a successful strategy for our company at all times and now, when money issues start to surface, we are happy that outsourcing helps us cut cost with no sacrifice of quality.
Kevin Chou is Author of this article from www.Colasoft.com.
About Colasoft Co., Ltd.
Ever since 2001, Colasoft has been dedicated in providing all-in-one and easy-to-use network sniffer software for network administrators and IT managers to monitor network activities, analyze network performance, enhance network security, and troubleshoot network problems. Up to now, more than 5000 customers in over 70 countries trust the flagship product – Colasoft network analyzer as their network monitoring and troubleshooting solution. Colasoft also offers four free network utilities: Colasoft Packet Builder, Colasoft Packet Player, Colasoft MAC Scanner, and Colasoft Ping Tool. Learn more about Colasoft and its solutions, please visit http://www.colasoft.com/.
Network Analyzer,Basic Tools of Network Administrators
Labels: colasoft, computer, network analyzer, network sniffer, network tool, packet sniffer, software, windows
 Network Analyzers are a valuable tool for both network administrators and hackers. There are many network analyzers on the market and one of the most sophisticated is the network analyzer from Colasoft
Network Analyzers are a valuable tool for both network administrators and hackers. There are many network analyzers on the market and one of the most sophisticated is the network analyzer from ColasoftNetwork Analyzers are one of the best tools a network administrator has at his or her disposal to analyze network traffic and to troubleshoot problems. On the other hand, when a network analyzer is in the wrong hands – i.e. hackers use it – this can cause quite a lot of damage to a company or an individual, especially if the victim hasn't taken the required protective measures. You see, as with many things in life, network analyzers can be a great tool to maintain a network, yet they can be very destructive, if misused.
Network Analyzers are very common, choose a best network analyzer for you. There are many network analyzers on the market and they range from free, to cheap, to expensive, from very simple, to advanced, to packed with features. Each type of network sniffers has its purposes and if you need a simple tool for quick results on a small network, you don't have to buy the most expensive network sniffers, no matter that they have tons of features. But in reality, if you need a network analyzer for professional use, low-end sniffers are not the answer and you need something more sophisticated, for example Colasoft Network Analyzer. Colasoft Network Analyzer is built around packet sniffing but includes many other useful features as well.
As any other network analyzer, the network analyzer from Colasoft, intercepts and logs traffic, transmitted within a network (or a network segment). A network analyzer can be really invisible because it monitors the network (almost) unobtrusively. Since a network analyzer just sniffs the packets without modifying them, it doesn't cause disturbances to alert the administrator that something is going on. Unless the administrator doesn't run an anti-sniffer, the traffic can be eavesdropped and nobody will know about it.
Of course, a good network administrator knows how to detect a network analyzer, so if you plan to get Colasoft network analyzer and use it in a malicious way, don't expect that this will go unnoticed. The network analyzer in the Colasoft Network Analyzer is not stealth but since anyway Colasoft Network Analyzer is intended for network troubleshooting, not network hacking, there is no reason to worry that the network sniffer is not hidden. When a network administrator uses a network analyzer in order to legitimately monitor network traffic, he or she doesn't need cover.
One of the most important features of a network analyzer is the protocols it can sniff. In this aspect Colasoft Network Analyzer is an unbeaten network analyzer because it can monitor over 300 protocols. Colasoft knows that when the packets of major protocols are not captured, this gives a wrong impression about the traffic in the network and that is why Colasoft Network Analyzer supports so many protocols. And no, the protocols Colasoft Network Analyzer can sniff are not exotic ones – they are protocols used frequently in networks.
Additionally, new and new protocols are added to the network analyzer from Colasoft, so even if your network uses some really rare protocols, which are currently not supported by Colasoft Network Analyzer, they could be added in the future. Well, if you expect that the network sniffer from Colasoft will sniff encrypted traffic, this will not happen because no network sniffer can do it!
How to sniff all images of a webpage?
Labels: colasoft, computer, network analyzer, network sniffer, network tool, packet sniffer, software, windows
Step 1. Open Log Settings
Log settings allows us to set up some conditions or exceptions whether or not record some logs in the Logs tab. If we want to display just images in the Logs tab, we must enable the HTTP Log conditions.
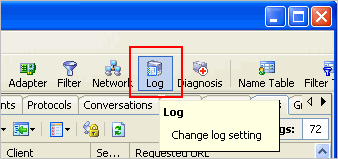
Step 2. Enable Http Log Conditions
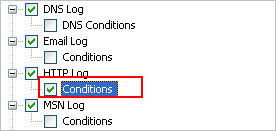
We must tick before Conditions to enable it
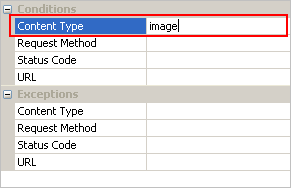
Step 3. Input "Image" into Content Type
On the right hand, lets’ input the content type in order to filter contents
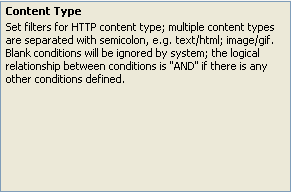
Here is an explanation of Content Type
Step 4. "OK" to Activate the Setting
Now we’ve done with the Log Settings, let’s see whether we can sniff all images of CNN.com index page. First of all, let’s start capturing with Colasoft network analyzer, then let’s input the URL into the address bar and start browsing.
Results start showing in the Logs Tab – Http Request Option, we can see all results are in image formats. We have successfully sniffed all the images on this webpage.
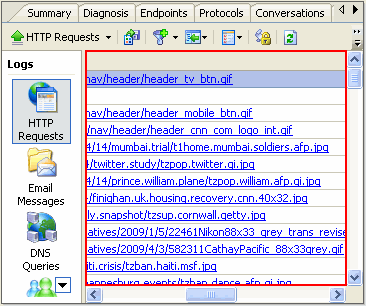
To view the image, we can click on the record, and it will be shown in a browser.

How to Protect Your Network with Network Analyzer?
Networks are large entities, even if they don't consist of thousands of machines. Large networks are especially vulnerable because they are a fruitful ground for attacks and hacking of all kinds. Even if a system administrator is a genius, he or she can't fight network security threats with bare hands.
Why Do You Need to Protect Your Network?
One of the major principles in network security is that a network is as secure as its weakest part is. In other words, it makes no sense to invest tons of money and spend many hours to secure some of the parts of a network, when there are small vulnerabilities that can be easily abused.
With networks small vulnerabilities are very common and even though one can never be sure that his or her network is secure, when no efforts in that direction are made, it is as sure as hell that this network is at risk. That is why it is absolutely clear that nobody can afford to leave a network unprotected. Fortunately, there are many tools, which help to protect a network and network analyzers are one of them.
How a network analyzer Can Protect Your Network?
Network analyzers (or network sniffers, as they are also called) can be one of the best tools you can use to protect your network. There are many types of network threats and there is no universal tool that can help you protect your network against all of them, so if you expect that a packet sniffer can safeguard your network against all kinds of threats, this is not so but it is a fact that a network sniffer can help you against many threats, both internal and external.
A network analyzer captures all the packets which go to and from your network and shows you their contents. While a network analyzer is helpless against encrypted traffic, with unencrypted traffic a network analyzer is an indispensable tool. When you have the chance to know what's going on in your network, you can easily spot the activities, which shouldn't be taking place.
For instance, if somebody is downloading files with BitTorrent, or is generating any other kind of substantial traffic, a network analyzer, such as Colasoft Network Analyzer, will display this immediately and you will know that you should take the adequate measures to stop it. Actually, a network analyzer allows to monitor all incoming and outgoing traffic and keep logs of this, so even if you don't react immediately when suspicious traffic occurs, all the traffic is logged and you can view it later.
Depending on the features of the network analyzer you have selected, you will have different options to protect your network. Some of the network sniffers with a rich feature set, for instance Colasoft Network sniffer, offers a lot in terms of traffic monitoring. Generally, even the network sniffers with less features allow to monitor suspicious activity at least from a given host or protocol.
One of the cases when network analyzer's don't offer much help is with encrypted traffic. This is a technical limitation and even though network analyzers can intercept encrypted packets, they can't break the encryption and show the actual content of the packet. However, when you are monitoring a network and you notice that there is unauthorized encrypted traffic (for instance from a given host), this should ring a bell that something not nice is probably going on and you should take the adequate measures to investigate what exactly is happening.
Colasoft network analyzer, The hottest Network Tools of IT administrators
Labels: colasoft, computer, network analyzer, network sniffer, network tool, packet sniffer, software, windows
 Overview
OverviewNot so hard for a freshman.
Auto diagnosis.
Real time capture.
If it's cheaper, I will definitely buy it!
After using Colasoft Network Analyzer, I found 3 features of this product:
a.supports the real-time capturing and monitoring
b.excellent capability of protocol analyzing (approximately 300 types) and packet decoding
c.Well, the most exciting part is the automatic expert diagnosing! That really saves so much money and time for me,and I do not worry about the solution of failure again!
Cost and performance are in desired level .
What It Is and What It Can Do
Colasoft network analyzer is an expert network analyzer designed for packet decoding and network diagnosis; it monitors the network traffic transmitted over a local host and a local network, with the ability of real time packet capture and accurate data analysis. Colasoft network analyzer makes your network operations completely transparent before you, letting you isolate and troubleshoot network problems quickly and efficiently. The flexible and intuitive user interface lets either IT professionals or novice users skilfully handle it in a few moments.
Easily understand how to use this network analyzer with samples provided with the Tool. Sample packets helps me a lot for my first time deployment by avoiding contacting the Technical Support during my initial days of using this tool.
For a Small Business Enterprise, This tool’s network diagnosis helps me to detect slow network and upgraded speed for better utilization.
I prefer this for a Medium Business Enterprise as troubleshooting network issues is simply superb.
For Medium and a Large Business Enterprises, Security is an issue .This network analyzer enhances Network Security by monitoring the network with Logs. As every packet is recorded and analyzed, loopholes can easily detect.
For every organization, security is a major concern. By using this tool Monitoring of Email Contents and Monitoring IMs, Chats is easy. Every information in Messegers, chats, HTTP Requests is logged .
Can easily find where the problem from the Packet Analysis without letting the user to report about his huge traffic.
For Internet Service Provider, this is very very useful tool. ISPs have problems of Server down issues due to huge traffics. By diagnosing with this tool, Server down issues can be reduced.
Prevent hibernation while capturing and view both IP Addresses and Hostnames. This is a good feature in upgraded version.
Colasoft network analyzer Supports Windows Vista-64 bit Edition. Able to identify and Analyze 300+ Network Protocols.
By going through the site www.colasoft.com, I came to know that Colasoft network analyzer Professional Edition available and used it for Analyses. It really good to use and operate. Everything is logged and my network usage is monitored.
Videos in the website help me to understand the ARP Attacks, Monitoring Network traffic. So I can protect my network now by identifying the deceived hosts and by identifying who is consuming maximum bandwidth in a Local Segment.
I can monitor the traffic either by protocol, IP or MAC Address. So much flexibility in using this network analyzer.
Internet Service Providers can use this tool for quick issue troubleshooting. Easy to identify problems and minimizes the time to service the customer.
The reports are displayed with Graphs and Tables .Viewing the connection in a matrix is wonderful and it is something special in Colasoft network analyzer. This pictorial epresentation is really good to sort out the issue by easily detecting.
Colasoft network analyzer has the tools that would not find in other network analyzers, including ping and scan IPs and MACS across the LAN.
Summary
Colasoft network analyzer is an easy-to-use and all-in-one tool for IT Network Administrator, IT Consultant and for a Security Manager in IT Company.